方向
| 篇数
|
Usability: Authentication
| 7
|
Cryptography: Attacks
| 7
|
Embedded Security & SW Sec
| 7
|
Usable Security and Privacy: User Perspectives
| 7
|
Cryptographic Proof Systems, Analysis, and Applications
| 7
|
Hardware Side Channel Attacks
| 7
|
Permissions and Passwords
| 7
|
Private Computation and Differential Privacy
| 7
|
Hardware Security
| 7
|
Usable Security and Privacy: Institutional Perspectives
| 7
|
Cryptocurrencies and Smart Contracts
| 7
|
Hardware Side Channel Defenses
| 6
|
Machine Learning: Backdoor and Poisoning
| 7
|
Program Analysis
| 7
|
Privacy Enhancing Technologies
| 7
|
Machine Learning: Adversarial Examples and Model Extraction
| 7
|
Automated Security Analysis of Source Code and Binaries
| 7
|
Secure Multiparty Computation
| 7
|
Adversarial Machine Learning: Defenses
| 7
|
Operating Systems Security
| 7
|
Web Security 1; Software Security
| 7
|
Machine Learning: Privacy Issues
| 7
|
Fuzzing
| 7
|
Web Security 2
| 6
|
Forensics and Diagnostics for Security and Voting
| 7
|
Internet and Network Security
| 5
|
Attacks
| 7
|
Research on Surveillance and Censorship
| 7
|
Malware and Program Analysis
| 7
|
Mobile System Security and Privacy
| 7
|
Phishing and the Malicious Web
| 7
|
DDOS; Wireless Security
| 7
|
Cryptography and the Cloud
| 6
|
Measurements of Fraud, Malware, Spam, and Other Abuse
| 6
|
IoT; Specialty Networking
| 6
|
TLS
| 6
|
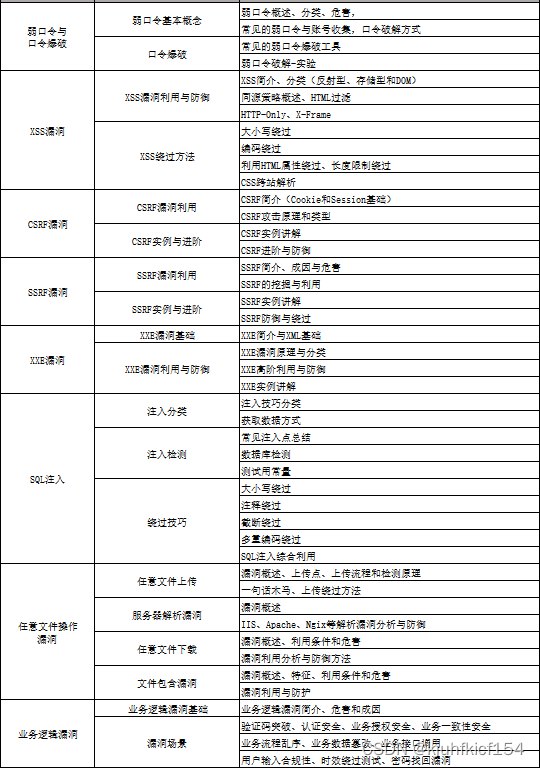
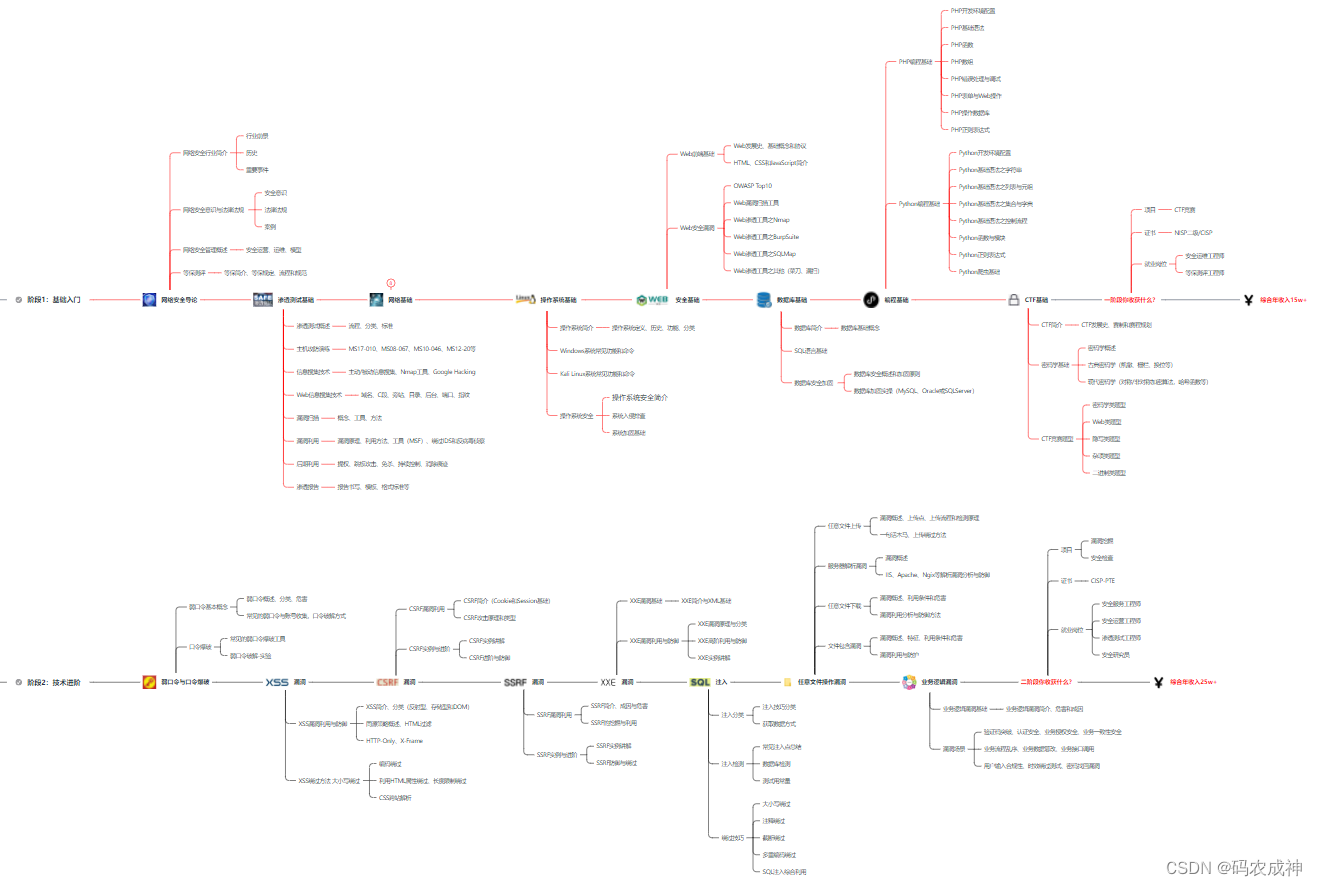
从上方表格可以看到,无论是硬件安全还是软件安全,无论是传统攻防还是AI安全,
 (IEEE Symposium on Security & Privacy)、USENIX Security(USENIX Security Symposium)。以下以USENIX Security 2021为例展示顶会的任命环境。
(IEEE Symposium on Security & Privacy)、USENIX Security(USENIX Security Symposium)。以下以USENIX Security 2021为例展示顶会的任命环境。