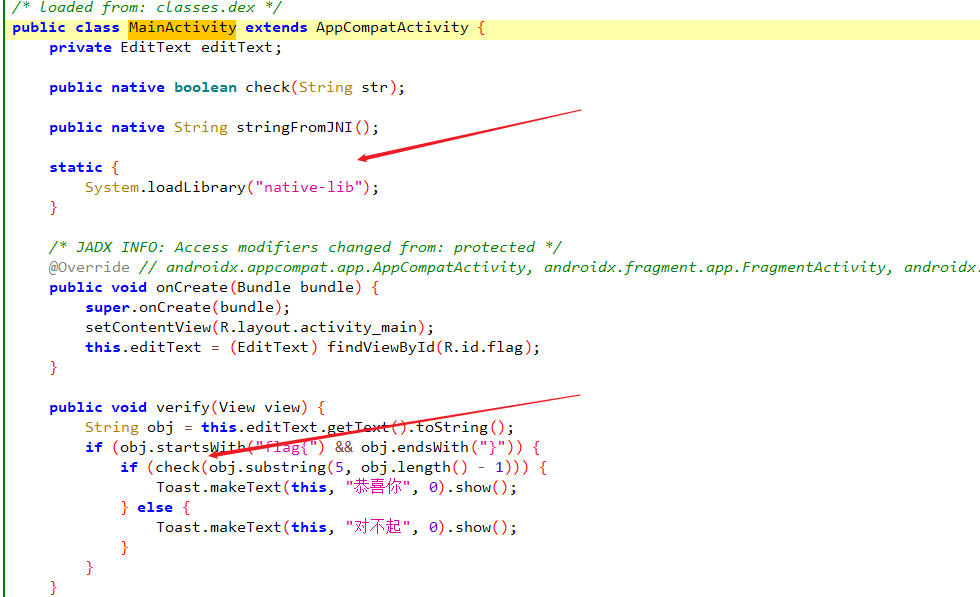
复制代码
- adb connect 127.0.0.1:7555
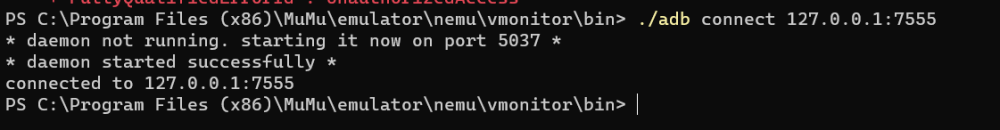
复制代码
- adb install test.apk
复制代码
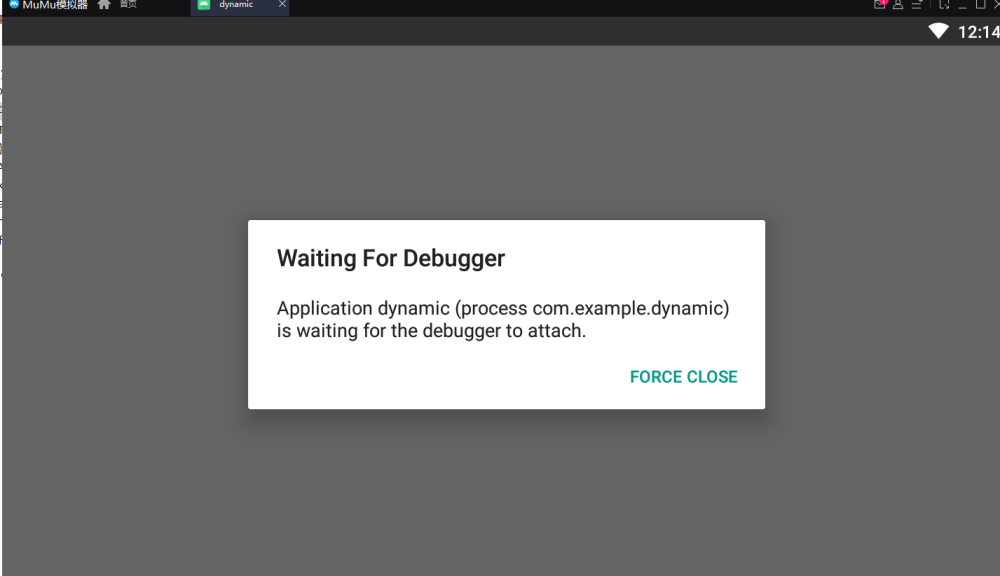
- ./adb shell am start -D -n com.example.dynamic/.MainActivity
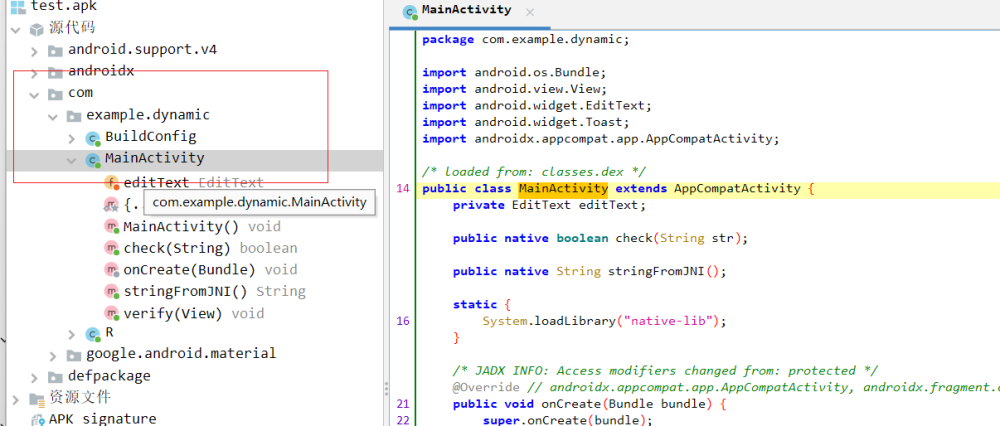
复制代码
- ./adb push android_x86_server /data/local/tmp

复制代码
- chmod +x android_x86_server
复制代码
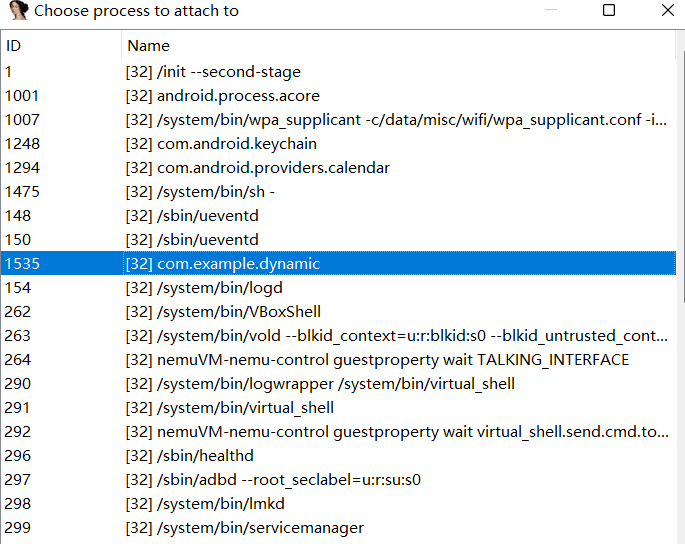
- ./adb.exe forward tcp:23946 tcp:23946
 ‘
‘
复制代码
- ./adb forward tcp:8700 jdwp:1535
复制代码
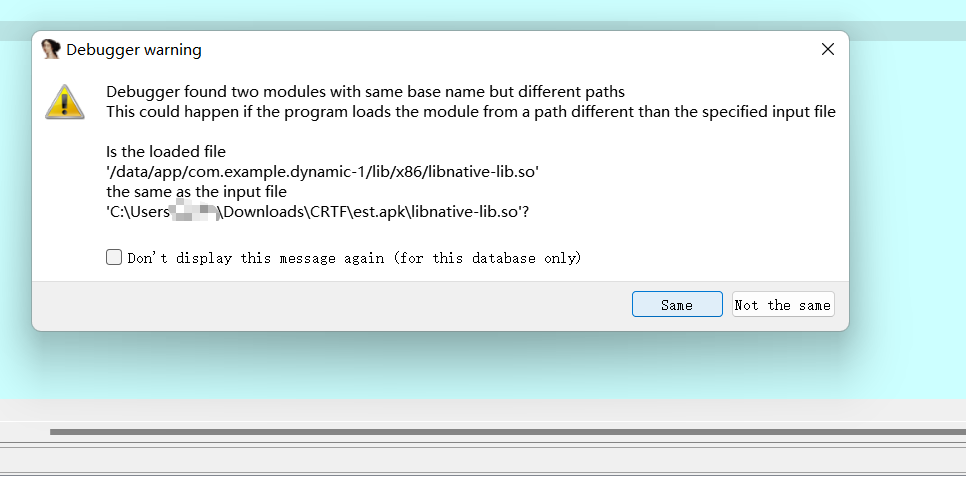
- jdb -connect com.sun.jdi.SocketAttach:hostname=127.0.0.1,port=8700
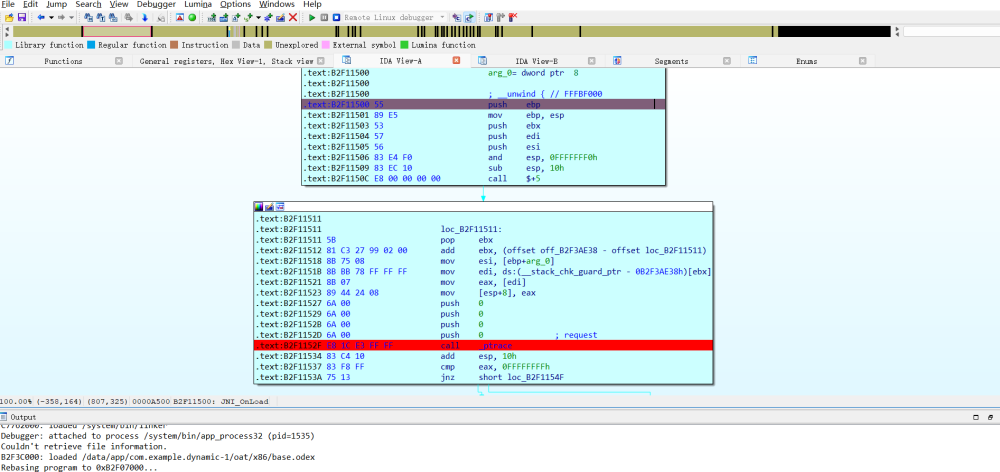

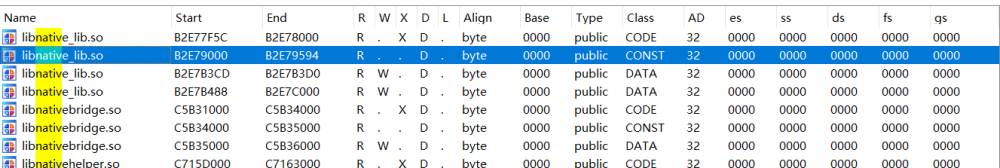
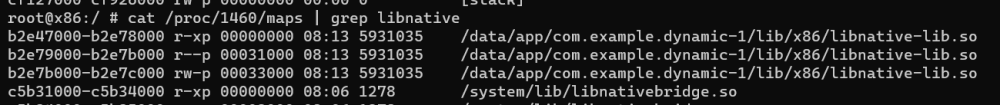
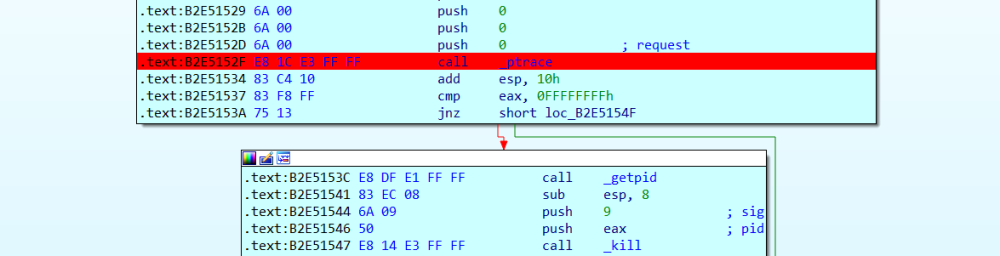

复制代码
- const char \*name: Java中声明的native方法。<br>const char \*signature:方法的签名。<br>void \*fnPtr: 函数指针
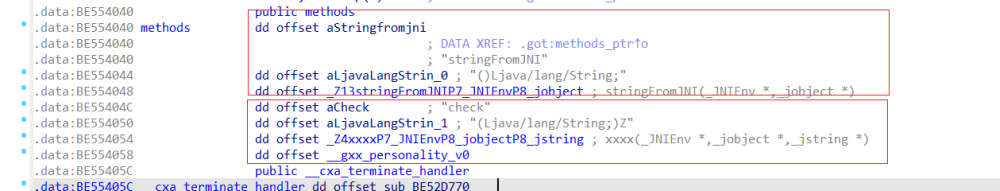
复制代码
- *(_OWORD *)v63 = xmmword_B2E6FA40;<br>.rodata:B2E6FA40 xmmword_B2E6FA40 xmmword 1032547698BADCFEEFCDAB8967452301h
复制代码
- .text:B2E51040 8D 84 24 B4 00 00 00 lea eax, [esp+0B4h]<br>.text:B2E51047 89 44 24 04 mov [esp+4], eax<br>.text:B2E5104B 8D 44 24 58 lea eax, [esp+58h]<br>.text:B2E5104F 89 04 24 mov [esp], eax<br>.text:B2E51052 E8 A9 E7 FF FF call __Z4ffffP7MD5_CTXPh ; ffff(MD5_CTX *,uchar *)
复制代码
- Python>esp=get_reg_value('esp')<br>Python>data=get_bytes(esp+0xb4,16)<br>Python>data.hex()<br>'a82e0cb168bfe134f22dbde167cf046c'
复制代码
- >>> import hashlib<br>>>> result=hashlib.md5("wojiushidaan0!!!".encode())<br>>>> result<br><md5 _hashlib.HASH object @ 0x00000167FF8BDEF0><br>>>> result.hexdigest()<br>'a82e0cb168bfe134f22dbde167cf046c'
复制代码
- .text:B2F11398 89 54 24 08 mov [esp+8], edx<br>.text:B2F1139C 8B 44 24 14 mov eax, [esp+14h]<br>.text:B2F113A0 89 44 24 04 mov [esp+4], eax ; s2<br>.text:B2F113A4 89 0C 24 mov [esp], ecx ; s1<br>.text:B2F113A7 E8 84 E4 FF FF call _memcmp
复制代码
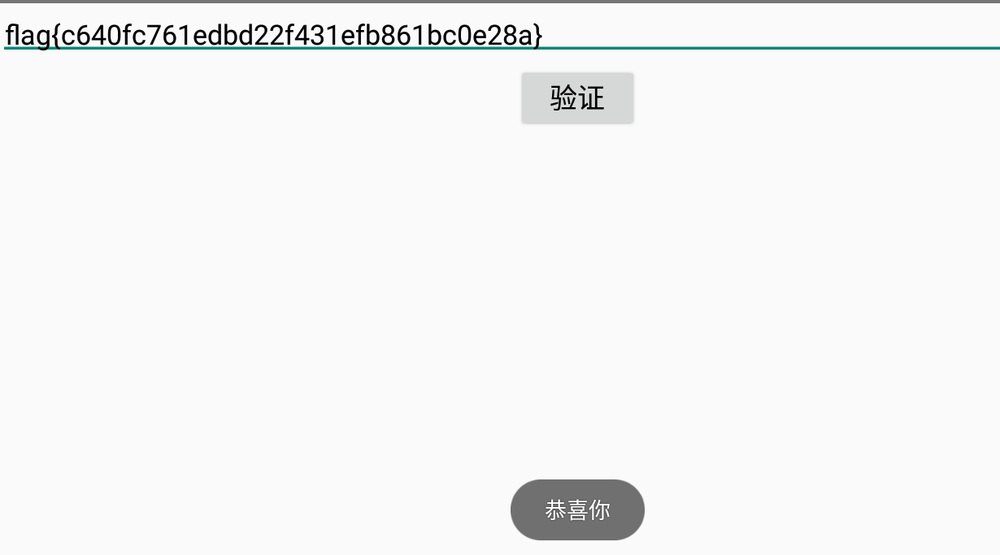
- b'c640fc761edbd22f431efb861bc0e28a'
复制代码
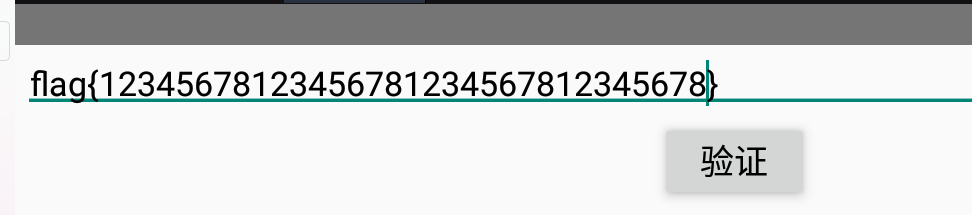
- b'12345678123456781234567812345678'
| 欢迎光临 IT评测·应用市场-qidao123.com技术社区 (https://dis.qidao123.com/) | Powered by Discuz! X3.4 |